Social engineering / noun
A technique that uses psychological manipulation, fraud or dishonesty to force people to disclose private, personal or corporate information, or to take particular action.
Social Engineering is a growing threat in the modern world, owing to the advancement and increasing awareness of cyber security controls. It takes a personal approach to breaking Cyber Security by praying on vulnerable people instead of vulnerable systems. Perpetrators can take time to build a trusted relationship with their victims in hope of getting them to reveal information, often with a view to take money from them. Social Engineering is especially dangerous as it simply relies upon human error, making it harder to trace.
Social engineering can take place across a range of channels: Social media, e-mail, phone calls and even face-to-face interactions. The attacker will identify their victim(s) and research them meticulously before making any contact. They work to identify feasibility of their plan being a success, susceptibility of the victim as well as the technology they use. Humans are often trusting by nature, making them the weakest link, compromising security in the course of social interaction. Social Engineering is becoming more sophisticated due to the breadth of information individuals share online, especially via Social Media. Attackers can likely find your date of birth, hobbies and interests, friends and family, place of work and colleagues. Having this information at their fingertips allows for them to establish a more convincing relationship.
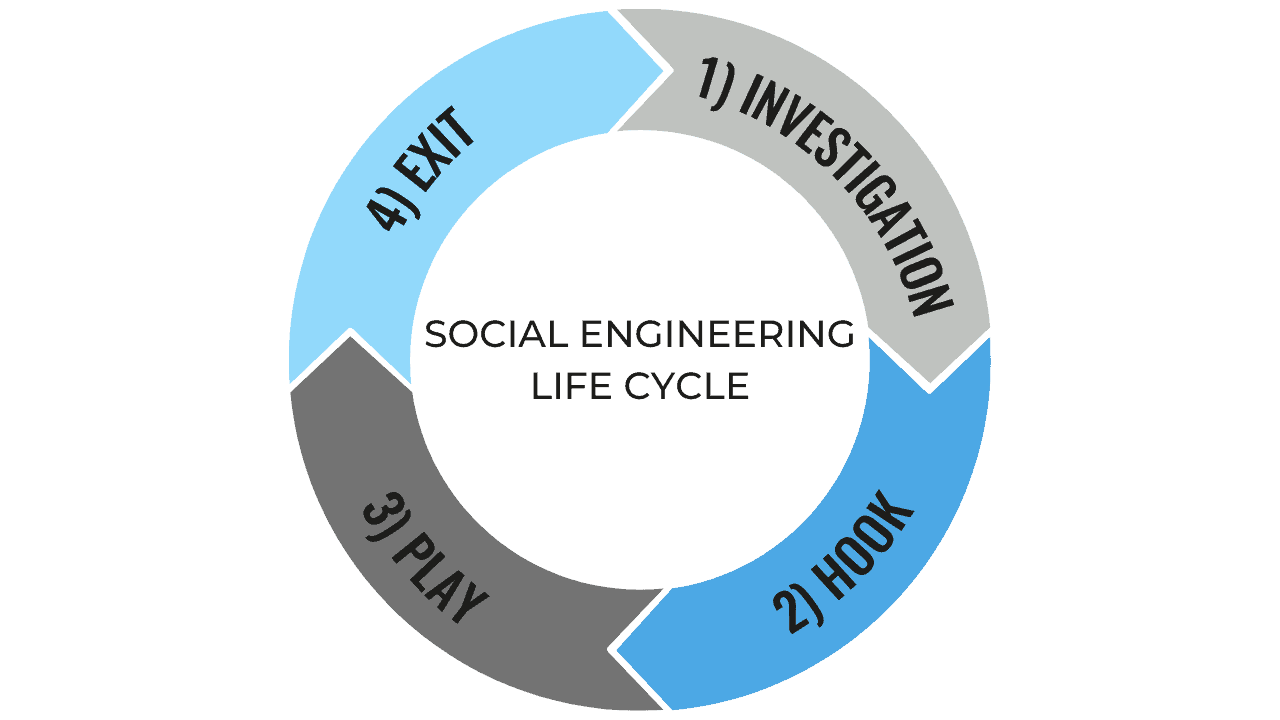
Pretexting is one of the more sinister methods of social engineering. The attacker will pose as a known friend, colleague, bank representative, government official or another person who could conceivably need to know specific information. They usually search for sensitive information such as full names, addresses, phone numbers, passwords or bank details. This could come via phishing emails or phone calls for example. Baiting comprises of a false promise or prompt of curiosity, inducing the victim to find out more and in doing so allowing information to be stolen via malware. Scareware pressurises people, inundating them with threats or false alarm, flustering them into letting their guard down. A common delivery method of scareware is convincing-looking pop-ups, with some even purporting to have detected viruses, prompting you to download malware disguised as cyber protection updates.
Higher profile attacks can be even more detailed, increased ambition comes with increased efforts. It can be more worthwhile (and harder to trace) for the attacker to put the time in building a more believable ruse, as opposed to working out how to hack a system. Whale phishing references targeting a ‘big fish’ such as a CEO or board member. These attacks could be socially engineered so that the attacker speaks to multiple employees to gather as much information as possible before contacting their real target. Sharing genuine facts makes messages seem more convincing, even if it’s as simple as mentioning the name of someone you work closely with. Recognition brings with it trust.
Vigilance is the best form of defence against social engineering. If something sounds too good to be true, or somebody is being overly charming or generous, stop and think before clicking a link or giving away information. The same applies in the event of scareware; stay calm and consider what you’ve been told in a measured fashion before taking any action. If there’s any semblance of doubt in your mind, speak to somebody else to get their viewpoint. Always ensure to report threats to your IT or cyber security provider.
Subscribe & share to spread the word on a range of topics covering Cyber Security, Risk & Compliance.
Clear Thinking partner with businesses to provide multi-layered secure and compliant IT solutions, including certifications, compliance, disaster recovery and more. Further details on our cyber security services, including vulnerability assessments, can be found here: https://clearthinking.co.uk/cyber-security/










